Introduction
Early this year, in January, the United States Department of Homeland Security canceled a project to build a virtual fence on the Southwest border, between the USA and Mexico. The project, called Project 28, sought to monitor a stretch of the border, using a combination of radar, high-resolution cameras, and wireless networking.
This brief will describe the high-level architecture of Project 28, list the reasons for its cancelation, and derive potential lessons, from the case, for Indian Homeland Security planners and agencies, when looking at solutions for border control of non-militarised borders.
Project 28
Project 28 was the name given to a US border protection programme that covered a 45-kilometre (28-mile) stretch of the US/Mexico border in southern Arizona. It was meant to be the first phase of a much larger programme to cover the entire US/Mexican border, called SBInet (Secure Border Initiative network).
The contract for the project was awarded to Boeing in September 2006, and covered a period of three years for building and operating the virtual fence, at a cost of USD 67 Million. What happened since was that the cost of the project escalated to USD 1 Billion, to build the virtual fence across 85 kilometres (53 miles) of the state’s border. As a result, the larger SBInet programme was cancelled, since it became obvious that the estimated programme cost of USD 7 Billion, for building a virtual fence along the entire border, was a gross underestimation.
The design of the virtual fence consists of six components:
Radar and Camera Tower
30-metre towers fitted with a Radar (Man-portable Surveillance and Target Acquisition Radar) and an EO/IR Camera, each, are strung along the border, at a short distance away from the actual border. These towers are connected to unmanned sensors in the vicinity. When migrants/smugglers cross the border, these towers convey real-time digital sensor data to the local Command & Control Centre. The initial plan envisaged nine such towers. The local Command & Control Centre can take direct control of the camera, and zoom in on the area that triggered the alert, to get further details on the nature of the intrusion.
Unattended Ground and Subterranean Sensors
An array of ground and subterranean sensors are installed at the border, and these are triggered when there is a crossing (person or vehicle). The sensors transmit the data to the closest tower.
Communications Fabric
The communications fabric allows the transfer of data between the sensors and the towers, and between the towers and the Command & Control Centres.
Command & Control Centre
This is a (privately) manned 24×7 operations centre that tracks alerts in its zone. The Command & Control Centre receives alerts from its corresponding towers. An operator then takes manual control of the camera on the tower that generated the alert, to get further information on the nature of the alert (persons or vehicle, armed or unarmed, etc.). The operator then transfers the information to the Border Patrol unit closest to the alert.
Border Patrol Vehicles with Mobile Data Terminals
The Border Patrol vehicles (land or air) are fitted with laptops and communication devices, in order to receive data from the Command & Control Centres. On receipt of a classified alert, the Border Patrol unit investigates the intrusion.
Physical Fences
At locations where there is an inhabited area very close to the border, physical fences are erected, in order to force the intruder to either scale the fence or go around it; thereby giving the system sufficient time to identify the intrusion, classify, and intercept the intruder, before it gets lost in the inhabited area.
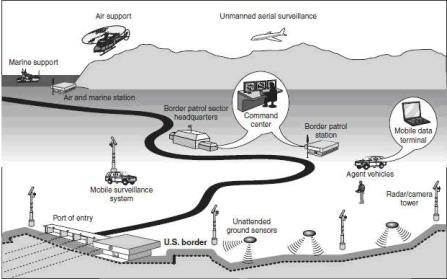
Project 28 Architecture Credit: http://www.globalsecurity.org/security/systems/sbinet.htm
A summary of the issues with Project 28 specifically, and the SBInet programme in general:
- The project cost, as mentioned in an earlier paragraph, escalated from an initial USD 67 Million to a final USD 1 Billion (albeit for a longer virtual fence)
- The efficacy of the virtual fence was questionable: given the rough terrain the fence had to traverse, the system was unreliable across a large stretch of the “fenced” border, either in terms of its ability to identify intrusions or in terms of the time taken to do so
- In the time between the sign-off and the cancellation of the contract, alternative technologies (drones) and approaches (more border patrol units, and working on specific intelligence inputs) were tried out, and it turned out that these delivered a better bang-for-the-buck
Lessons from Project 28
The lessons from the failure of Project 28, and of the SBInet programme, are salient to the Indian situation too, regardless of the difference in approaches to addressing Homeland Security issues: in stark contrast to the US “over-reliance on technology” approach, the Indian approach is one of “throwing persons at a problem”.
- Robustness of technologies
The technologies that are selected for use in a virtual fence project have to be tried and tested. It is preferable going in for a robust technology that may be not cutting-edge, than a cutting-edge technology that keeps failing in the field. In addition, a sensor technology with a high FAR/NAR (False Alarm Rate/Nuisance Alarm Rate) will soon fall into disuse, as the user loses trust in it and ignores any alarms generated by that sensor. - User-friendliness
The technology has to be simple to use (as few steps as possible), and should deliver the required information without much effort. Often, the device being deployed in the field either requires an in-depth knowledge of matters technical or delivers data that is so coarse that it requires significant analysis from the user to convert the data to actionable information. In the case of Project 28, it turned out that the EO/IR camera on the tower took a long time to be manually PTZed to the spot that generated the alert, and when it finally focused on the spot, the captured images were fuzzy. - Horses for courses
Each border terrain requires its own combination of sensor technologies and communications network solutions. It is impractical to decree a one-fits-all solution for the entire border. A user needs to shortlist a suite of technologies and then decide on the best combination, for a terrain, based on field trials. Looking at successful implementations in another country or region will not necessarily result in a successful implementation at home. For example, Israel’s approach to border control (very successful) may not be practical for India’s operating conditions. - Implementation time
Projects such as these cannot be executed over a timeframe of years. In the time it takes to complete the project, newer technologies or more effective methodologies may reach maturity, leaving the project open to the charge of being obsolete as soon as it is operational. When the user shortlists a suite of technologies, it needs to do so on the understanding that these can be implemented in weeks rather than in months and years. - Technology is not a panacea for all problems
Sometimes, throwing more persons at a problem is more effective than solving it using technology. In the case of the US border control problem, it was found out that increasing the number of Border Patrol units, directed based on specific field intelligence, achieved far better results than the virtual fence. In India there is a tendency to throw persons at a problem, but in attempting to correct this, a user should not stray to the other extreme of being overly dependent on technology.
Conclusion
Virtual fencing is a valuable weapon in the armoury of Homeland Security planners looking at border control, but it should be seen as complementing other such weapons such as field patrolling, physical fencing, and intelligence gathering. Focusing on just one approach could result in a system that is not as effective as it could be or as expected.
Mistral offers virtual fencing solutions that address a wide range of operating environments through a mix of tried and tested technologies.



