Introduction
George Orwell’s novel “1984”, describes a society under the control of a single party, manifested in Big Brother, and characterized by pervasive government surveillance and public mind control; the latter through constant propaganda and revisionism of the past. Although “1984” was Orwell’s warning of the perils of the Communist form of government, one facet of Orwellian society – pervasive government surveillance – seems to be quietly establishing itself in the anti-thesis of the Communist form of government; today’s Western liberal democracy.
This brief examines recent trends and new developments in the area of surveillance that could see totalitarian-governed society characteristics becoming accepted features of liberal societies.
The Terrorism Bogey and The Panopticon
Until terrorism from Islamic fundamentalists invaded the shores of the USA and Europe, and threatened the shores of similar societies such as Australia and New Zealand – for the purpose of brevity, this group will hereinafter be referred to as Western Society – Western Society was quite blasé about the perils of the radicalization (religious or ethnic) of sections of societies in various parts of the world, despite protestations from countries, such as India, which had been at the receiving end of the activities of such radicalized groups. The response of Western Society was that the countries protesting were imperfect democracies and that the activities of such radical groups were quasi-legitimate efforts at improving the lot of the oppressed in these democracies.
Following the 11 September 2001 (9/11) attacks in the USA, though, Western Society’s response to radical terrorism, mostly of the Islamic fundamentalist variety, has been to shift from the liberal “loathe to trample on one’s freedom-of-speech” attitude to an insular “racial-profiling is justified” attitude. The US government has used the terrorism bogey, post 9/11, to legislate unprecedented surveillance measures abroad and, more worryingly, at home, to ensure that such an event never happens again in the country.
Under the guise of controlling terrorist activities, the level of domestic surveillance, in the USA, has increased substantially, since 9/11. Technologies and techniques that have been tried and tested, and refined, in overseas theatres of conflict, are now being deployed on the citizens of the country, who have little knowledge about the potency, pervasiveness, and persistence of new surveillance technologies: and, dangerously, what happens in the USA gradually percolates to the rest of the world.
There is a real danger of society, slowly but surely, being transformed to the English philosopher Jeremy Bentham’s conception of an institution (a prison) where the inmates are constantly under observation: the Panopticon. In his words, the Panopticon is “a new mode of obtaining power of mind over mind, in a quantity hitherto without example.”
Potent, Pervasive, and Persistent Surveillance Technologies
The new surveillance technologies are evolutionary developments on existing technologies. In some cases the developers of the technology had no prior surveillance functionality in mind: it’s just that the technology lent itself so well for surveillance purposes.
Eyes-in-the-Sky
There is a move towards developing a new breed of drones that will patrol the skies in the stratosphere (12,000+ metres to 45,000+ metres), with arrays of extremely high-resolution cameras recording the daily activities of populations of entire cities. The stratosphere is a relatively empty part of the atmosphere, and it is relatively less expensive to launch aircraft that circulate in the stratosphere. In addition, the flexibility of retrieving and reusing the aircraft, and the lower cost associated with bringing the aircraft back to terra firma, make the concept of stratospheric aircraft a lot more attractive than surveillance satellites. These drones will be glider-looking, solar-powered aircraft, running on energy, collected during the day, to drive their propellers. The drones will be able to record the movements of individuals, the routes and speeds of vehicles, the time when lights switch on in a house: effectively Google Street View at a city level, 24 hours a day, 365 days a year.
In September 2010, DARPA (Defense Advanced Research Projects Agency), USA, awarded a contract to Boeing to develop a craft that will be able to fly above 18,000+ metres, for a duration of five years non-stop, carrying a sensor and associated equipment payload of approximately 500 kgs. Boeing plans to start test flights in 2013.
 |
| Figure 2: Solar eagle Credit: Boeing |
Repository of all Digital CommunicationsA recent report by James Bumford, who writes extensively on the United States National Security Agency (NSA), describes a project to build the largest data aggregation and analysis centre of its kind, in the world. When operational, in late 2013, the centre will intercept, decipher (or attempt to decipher), and analyse every single stream of digital communications transmitted over satellite links and underground/undersea optical cables, emanating both outside the USA and within the country. These digital streams will be collected in repositories and data-mined for useful information – potential terrorist threats, spy networks, illicit financial dealings, transit of contraband goods, etc. The facility, when fully operational, will have the capacity to handle up to 20 TB of intercepts a minute and, perhaps, store up to a yottabyte (1024 bytes) of data.
The United States NSA’s plans are but the most ambitious among a host of government agencies in other countries aiming to conduct surveillance on their own citizens, using tools available from commercial organisations. The Wikileaks Spy Files describe the domestic interception capabilities in 25 countries (including India), and reveal the details of which companies are making billions selling sophisticated tracking tools to government buyers.
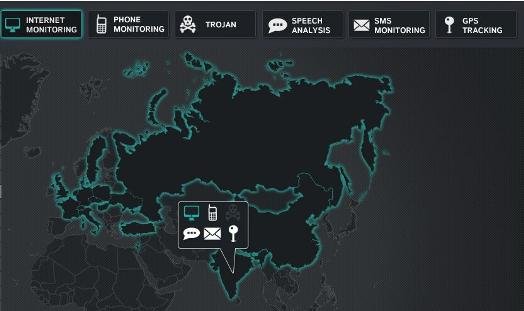 |
| Figure 3: The Spyfiles – The Map Credit: Wikileaks http://wikileaks.org/The-Spyfiles-The-Map.html |
The Cloud
Cloud computing and social networking are the hottest enablers on the Internet today: enabling anything from a SME to run enterprise-grade applications without having to pay enterprise-size license fees, to enabling content creators and consumers to transparently share and interact on digital content. The Cloud is also a huge repository of digital content and data, there for the asking by any interested government agency with sufficient clout to force the data aggregator to hand over the data.
As mentioned in an earlier Tech. Brief, May 2011 – Using Social Networking Sites and Tools for Intelligence-gathering – Julian Assange, Wikileaks editor-in-chief and main spokesperson, said that US intelligence and law-enforcement agencies have access to all information on all major social networks and many Internet-based companies.
The fact of the matter is that any user who decides to share data on the Web also runs the risk of seeing this data being used by surveillance agencies for purposes the user had not originally intended, privacy protection claims by the service provider notwithstanding. Recent changes in Google’s privacy rules, which came into effect on 1 March 2012, allowing Google to associate searches or any other activities on Google’s cloud with the logged-in user, of its mail or social networking service, makes it easier for surveillance agencies to obtain aggregated information on a user; although the intent behind the change in policy was merely to better leverage the commercial opportunities of selling the user something.
 |
| Figure 4: Digital communications interception capabilities, country-wise, as per Wikileaks. Credit: Wikileaks http://wikileaks.org/ |
Causes for Concern
The problem with the pervasive and persistent monitoring of societies, under the guise of ensuring their safety, is that the data gathered, for seemingly legitimate reasons, can so easily be misused.
- The Whole is Greater than the Sum of its Parts
The surveillance data, collected separately, carries information of some value. However, when combined with data from other sources, the value of the information increases manifold. Once in possession of the data, government agencies can cross-index data from the various sources (location-based data, cellphone conversations, e-mail communications, video streams, etc.) to build a profile of a citizen that can easily transgress the blurry line between public safety and personal liberty. - Privacy & Confidentiality
The privacy of an individual is no longer sacrosanct, when detailed profiles of citizens are built up using remote surveillance data; especially when the profiles contain information that have no bearing on the purpose for which the surveillance data was collected (public safety or national interests). The agencies that intercept and analyse such data show a greater predilection to misuse such private information, given the human psychological trait of treating the subject of such disembodied information as not meriting any empathy. - Over-reliance on technology
The increasing use of potent technology, to carry out surveillance of a nation’s own citizens carries the danger of alienating the analysers of the information from the citizenry, and vice-versa. There is also the danger of analyzing situations in black-and-white, and dispensing with a shades-of-gray approach, when the analyser is one or two steps removed from the object of the analysis. - Where does one stop? The Law of Diminishing Returns
At some point, the increase in surveillance no longer delivers additional benefits with respect to the stated purposes for which the surveillance was carried out. London is the city with the most no. of surveillance cameras installed, in the world; but despite the massive increase in surveillance cameras from the 1980s, there has been no appreciable drop in crime rates. Looking at the initial surge in benefits, after implementation of a surveillance technology, decision-makers tend to assume a similar scale of improvement with the addition of further surveillance.
Conclusion
The Homeland Security Tech. Briefs over the past couple of years have focused on homeland security issues and on leveraging existing and upcoming technologies to address these issues. The underlying belief in all the briefs was that the technology would be wisely applied, and that the data gathered from the application of the technology, handled with due care and concern.
This last brief is meant as a warning about the potential overreach in the application of technology, to address homeland security issues, and in the use of surveillance data, by the agencies entrusted with ensuring public safety and protecting national interests. Noble causes should be fought through fair means, even if the fight is that much harder; else, the causes may no longer be worth fighting for.



